If you’ve been following the analytics world lately, you’ve probably noticed a shift. It’s no longer enough to simply collect data and hope for the best when it comes to privacy. Regulations are tightening, users are demanding transparency, and the old playbook of “collect everything, figure it out later” is officially dead.
Enter privacy-enhancing technologies — or PETs, as they’re known in the industry. These aren’t just another buzzword to add to your marketing deck. They represent a fundamental rethinking of how we collect, process, and extract value from data without compromising individual privacy.
In my guide to the future of web analytics, I touched on how these technologies are reshaping our entire field. Now let’s go deeper. Because understanding PETs isn’t optional anymore — it’s becoming a core competency for anyone working with data.
What Are Privacy-Enhancing Technologies?
Privacy-enhancing technologies are a broad family of tools, techniques, and approaches that allow organizations to collect, analyze, and share data while mathematically or architecturally guaranteeing that individual privacy is preserved. The key word there is guaranteeing — not hoping, not promising in a privacy policy, but providing provable, technical assurances.
Unlike traditional anonymization (which we’ll compare later), PETs don’t just strip out obvious identifiers and call it a day. They use cryptographic methods, statistical techniques, and clever system designs to ensure that useful insights can be extracted from data without ever exposing the underlying personal information.
Think of it this way: traditional analytics is like reading someone’s diary to understand their habits. PETs let you understand the habits without ever opening the diary.
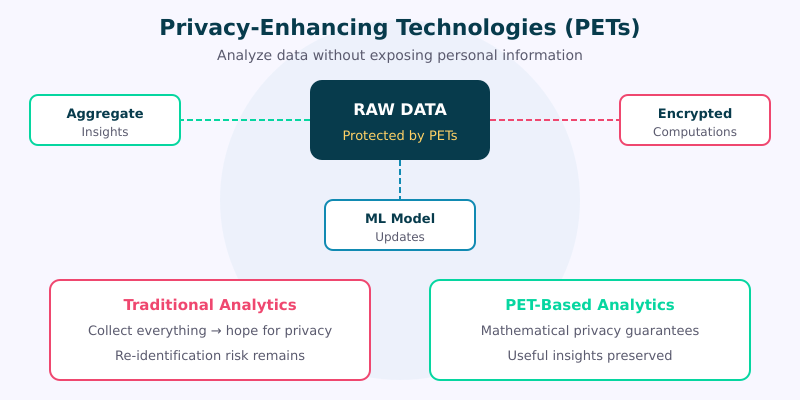
The concept isn’t entirely new — differential privacy research dates back to 2006 — but the practical implementation and commercial adoption of PETs has exploded in the last few years. GDPR, CCPA, the deprecation of third-party cookies, and growing public awareness of data misuse have all created the perfect storm for PETs to move from academic research into production systems.
The Five Core PET Categories
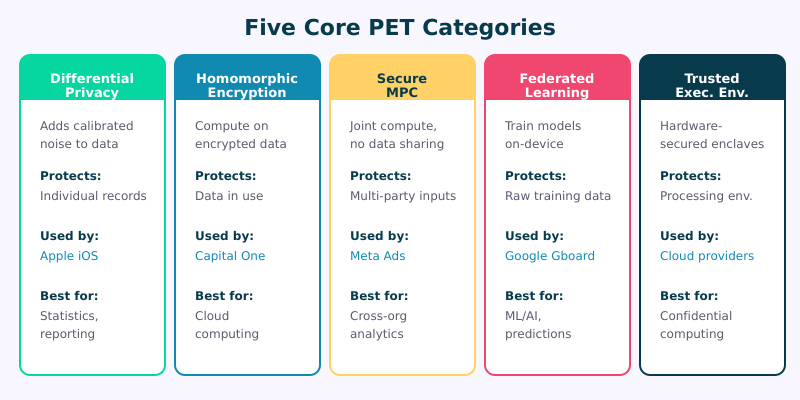
While the PET landscape is broad, most technologies fall into five major categories. Each solves a different piece of the privacy puzzle, and in practice, organizations often combine multiple approaches.
1. Differential Privacy
Differential privacy adds carefully calibrated mathematical noise to datasets or query results, making it impossible to determine whether any single individual’s data was included. The beauty of differential privacy is that the noise is precisely tuned: enough to protect individuals, but not so much that it destroys the statistical utility of the data.
Imagine you’re measuring the average time users spend on your website. With differential privacy, you’d add a small random value to each measurement before computing the average. The aggregate result stays accurate (the random noise cancels out across thousands of users), but no single user’s exact session time can be reverse-engineered.
Best for: statistical analysis, reporting, publishing aggregate data, training machine learning models.
2. Homomorphic Encryption
This is the one that sounds like science fiction — and honestly, it kind of is. Homomorphic encryption allows computations to be performed directly on encrypted data, producing encrypted results that, when decrypted, match what you’d get from processing the unencrypted data.
In practical terms: a cloud provider can analyze your customer data without ever seeing it in plaintext. You send encrypted data, they run calculations on the ciphertext, and send back encrypted results that only you can decrypt.
Best for: cloud computing on sensitive data, outsourced analytics, secure data storage with computation.
3. Secure Multi-Party Computation (MPC)
Secure MPC allows multiple parties to jointly compute a function over their combined data without any party revealing their individual inputs to the others. Everyone learns the result, but nobody learns anything about anyone else’s data beyond what the result itself reveals.
This is particularly relevant for analytics scenarios where competitors or partners need to combine data for mutual benefit — like measuring ad effectiveness across platforms — without exposing their proprietary datasets to each other.
Best for: cross-organization analytics, ad measurement, benchmarking, collaborative research.
4. Federated Learning
Rather than centralizing data for analysis, federated learning brings the algorithm to the data. Machine learning models are trained locally on each device or server, and only the model updates (not the raw data) are shared and aggregated centrally.
Your phone’s keyboard predictions are a perfect example. The model learns from your typing patterns locally, shares only the learned improvements with a central server, and your actual keystrokes never leave your device.
Best for: on-device machine learning, predictive analytics, personalization without centralized data collection.
5. Trusted Execution Environments (TEEs)
TEEs create isolated, hardware-secured enclaves within processors where data can be processed in plaintext but is protected from everything outside the enclave — including the operating system, other applications, and even the server administrator.
Think of a TEE as a locked room inside a building. The building owner can’t see what happens inside the room, can’t access its contents, and can’t tamper with the process. The data goes in, results come out, and nothing in between is visible or modifiable.
Best for: secure cloud processing, confidential computing, multi-party data collaboration.
Why PETs Matter for Analytics
Let’s be honest about where the analytics industry stands. The old model was simple: drop a JavaScript tracker on your site, collect everything you can, store it indefinitely, and mine it for insights. That model is broken — legally, ethically, and increasingly, technically.
Here’s why PETs aren’t just nice-to-have for analytics professionals:
Regulatory compliance is getting harder, not easier. GDPR, CCPA/CPRA, Brazil’s LGPD, and dozens of other regulations demand data minimization and purpose limitation. PETs let you comply by design rather than by policy. When you’re using differential privacy, there’s no personal data to breach, misuse, or fail to delete upon request.
Consent fatigue is killing your data quality. As users get bombarded with cookie banners and consent popups, opt-in rates are plummeting. Many privacy-compliant analytics solutions can operate without consent precisely because they employ PET principles — there’s nothing personal to consent to.
Third-party cookies are gone. The tracking infrastructure that powered cross-site analytics for two decades is disappearing. PETs like secure MPC and data clean rooms provide legitimate alternatives for cross-site measurement without invasive tracking.
Data breaches are existential threats. If you never collect or store personal data in plaintext, there’s nothing to breach. PETs reduce your attack surface dramatically — homomorphic encryption means even a complete database theft yields nothing useful to attackers.
Gartner projected that 60% of large organizations would use at least one PET technique by 2025, up from less than 10% in 2021. That prediction has largely come true. If you’re not exploring PETs, you’re falling behind.
PETs in Practice: Real-World Examples
PETs aren’t theoretical. The biggest names in tech are already deploying them at scale.
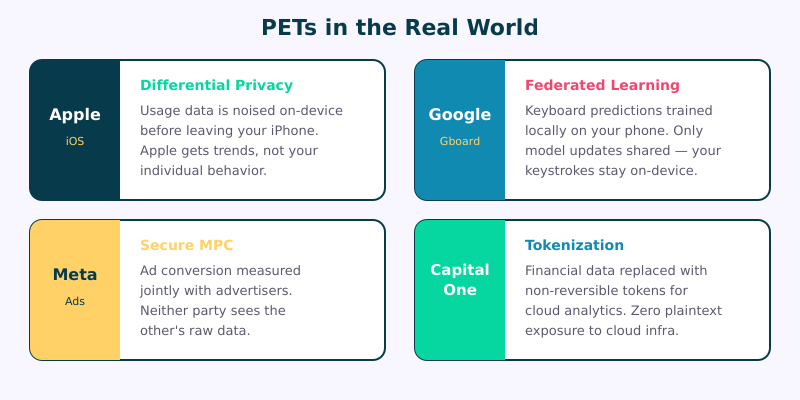
Apple and Differential Privacy. Apple has been using differential privacy for iOS analytics since 2016. When your iPhone collects usage data — popular emoji, Safari crash statistics, QuickType suggestions — it applies local differential privacy before the data ever leaves your device. Apple gets the aggregate trends it needs to improve products; your individual behavior stays on your phone.
Google and Federated Learning. Google pioneered practical federated learning with Gboard, its mobile keyboard app. The predictive model improves from millions of users’ typing patterns without Google ever seeing what any individual user actually typed. They’ve since expanded this approach to other on-device features across Android.
Meta and Secure MPC. Meta (formerly Facebook) uses secure multi-party computation for ad measurement and conversion attribution. Advertisers need to know if their Facebook ads drive purchases, but neither Meta nor the advertiser should see each other’s raw data. Secure MPC lets them jointly compute conversion metrics without exposing user-level data to either party.
Capital One and Tokenization. Capital One uses advanced tokenization — a PET technique that replaces sensitive data with non-reversible tokens — to secure financial data in cloud environments. This allows them to leverage cloud computing for analytics while ensuring that customer financial data is never exposed in plaintext to cloud infrastructure.
The European Health Data Space. The European Health Data Space Regulation, which advanced significantly in early 2025, creates a framework for sharing health data across EU member states for research purposes. PETs — particularly synthetic data generation and secure computation — are central to enabling researchers to work with anonymized health datasets while maintaining ironclad patient privacy protections.
Data Clean Rooms. Companies like Snowflake, Google, and Amazon now offer data clean rooms — controlled environments where multiple parties can combine and analyze their data without any party accessing the other’s raw information. These environments typically combine multiple PET techniques (encryption, access controls, differential privacy) to ensure privacy. For analytics professionals, data clean rooms are becoming a primary tool for the kind of cross-platform measurement that used to rely on third-party cookies.
PETs vs Traditional Anonymization
This is where a lot of organizations get tripped up. Traditional anonymization — stripping names, email addresses, IP addresses, and other obvious identifiers from datasets — was the go-to approach for decades. But it has a fatal flaw: it doesn’t actually work.
Research has repeatedly shown that “anonymized” datasets can be re-identified with alarming ease. A famous 2006 study re-identified Netflix users from their anonymized movie ratings. In 2013, researchers showed that just four approximate location data points were enough to uniquely identify 95% of individuals in a 1.5-million-person dataset. More recently, browsing history analysis has achieved re-identification rates above 80% even from supposedly anonymized datasets.
Here’s how PETs fundamentally differ:
- Traditional anonymization removes identifiers and hopes that’s enough. PETs provide mathematical guarantees about what can and cannot be inferred.
- Traditional anonymization is a one-time transformation that can be reversed with enough auxiliary data. PETs like differential privacy are provably irreversible — the noise can’t be removed.
- Traditional anonymization operates on data at rest. PETs can protect data during computation (homomorphic encryption, TEEs) and during sharing (secure MPC).
- Traditional anonymization often degrades data quality significantly. PETs are designed to preserve utility while protecting privacy — you don’t have to choose between useful data and private data.
This doesn’t mean traditional anonymization is useless — it’s still a reasonable first step. But relying on it alone is increasingly seen as insufficient by regulators and privacy experts. PETs provide the kind of rigorous protection that modern privacy laws actually demand.
The PET Market: Size and Growth
The PET market is booming, and the numbers tell a compelling story about where the industry is headed.
Market estimates vary by research firm, but the consensus range puts the PET market at $3.85 to $5.62 billion in 2025, with projections reaching $12.26 billion by 2030 — a compound annual growth rate of approximately 19.8%.
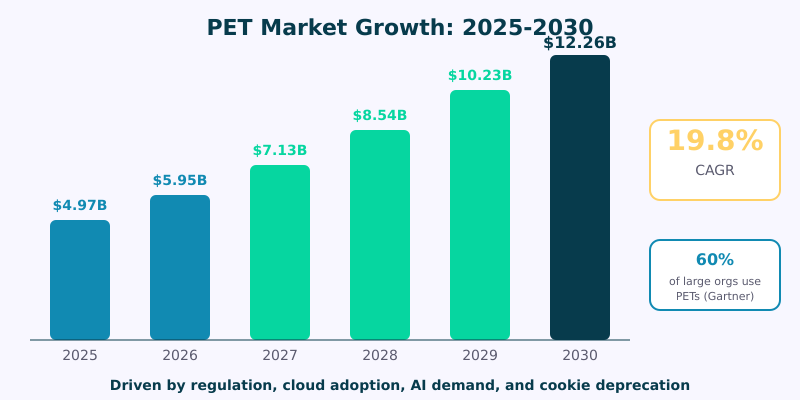
Several forces are driving this growth:
- Regulatory pressure: Every new privacy law creates demand for technologies that enable compliance by design.
- Cloud adoption: As organizations move sensitive workloads to the cloud, they need ways to compute on data without trusting the cloud provider with plaintext access.
- AI/ML demand: Training machine learning models requires massive datasets. PETs like federated learning and differential privacy enable model training without centralizing sensitive data.
- Cookie deprecation: The end of third-party cookies has accelerated investment in privacy-preserving measurement and attribution technologies.
- Data collaboration: Organizations increasingly need to share data with partners, vendors, and researchers — PETs make this possible without the liability of exposing raw data.
For analytics professionals, the takeaway is clear: this isn’t a niche market. PETs are becoming core infrastructure for any organization that works with data. The alternatives to Google Analytics that are gaining market share — tools like Plausible, Fathom, and Matomo — already embody PET principles through data minimization, aggregation-first processing, and zero personal data collection.
How to Start with PETs
You don’t need a PhD in cryptography to begin incorporating PETs into your analytics practice. Here’s a practical roadmap:
Step 1: Audit your data flows. Before you can apply PETs, you need to understand what data you’re collecting, where it goes, and who accesses it. Map every data touchpoint in your analytics stack — from collection scripts to storage to dashboards.
Step 2: Identify your biggest risks. Where are you collecting or storing personal data that you don’t strictly need? Where are you sharing data with third parties? Where would a breach be most damaging? These are your priority areas for PET adoption.
Step 3: Start with data minimization. The simplest and most immediately impactful PET principle is collecting less data in the first place. Review every data field you collect and ask: “Do we actually use this for a specific, defined purpose?” If the answer is no, stop collecting it.
Step 4: Adopt privacy-first tools. Switch to analytics platforms that have PET principles built in. Cookie-free, privacy-first analytics tools already implement aggregation, data minimization, and in some cases differential privacy at the collection level. This is the easiest way to get PET benefits without building custom infrastructure.
Step 5: Explore data clean rooms for collaboration. If you need cross-platform or cross-organization analytics, investigate data clean room solutions from major cloud providers. These offer practical PET-based collaboration without requiring you to build your own cryptographic infrastructure.
Step 6: Build internal expertise. Designate someone on your team to become your PET specialist. The field is evolving rapidly, and having someone who can evaluate new tools, understand vendor claims, and guide implementation decisions will pay off enormously as PETs become standard practice.
FAQ
Do PETs completely eliminate privacy risk?
No technology eliminates risk entirely. PETs significantly reduce privacy risk and can provide mathematical guarantees about specific types of information leakage, but they must be implemented correctly and as part of a broader privacy program. A poorly configured differential privacy system, for example, might add too little noise to provide meaningful protection. PETs are powerful tools, but they require expertise to deploy effectively.
Are PETs too expensive for small and mid-size businesses?
Not necessarily. The most accessible form of PET adoption — switching to privacy-first analytics tools — can actually save money compared to running a full Google Analytics 4 implementation with consent management platforms, cookie banners, and GDPR compliance overhead. More advanced PETs like homomorphic encryption do require significant investment, but data clean rooms and differential privacy tools are increasingly available as affordable SaaS products.
Can PETs work with existing analytics platforms?
It depends on the platform and the specific PET. Some PETs, like differential privacy, can be applied as a layer on top of existing data pipelines. Data clean rooms are designed to integrate with existing data warehouses. However, some PETs require fundamental changes to how data is collected and processed. The most practical approach for most organizations is to adopt analytics tools that have PET principles built in from the ground up, rather than trying to retrofit them onto legacy systems.
What’s the difference between PETs and zero-knowledge proofs?
Zero-knowledge proofs (ZKPs) are actually a type of PET. They allow one party to prove to another that a statement is true without revealing any information beyond the truth of the statement itself. For example, you could prove that a user is over 18 without revealing their actual age or birthdate. ZKPs are particularly relevant for identity verification and access control scenarios, and they’re increasingly being integrated into blockchain and decentralized identity systems.
The Bottom Line
Privacy-enhancing technologies aren’t coming — they’re here. From Apple’s differential privacy in every iPhone to Meta’s secure MPC powering ad measurement to the data clean rooms being adopted across the industry, PETs have moved from academic curiosity to production infrastructure.
For analytics professionals, the question isn’t whether to engage with PETs, but how quickly you can integrate them into your practice. The organizations that master these technologies will have a massive competitive advantage: they’ll be able to extract the same (or better) insights from data while dramatically reducing privacy risk, regulatory exposure, and the operational burden of managing personal information.
The future of analytics is privacy-first by design, not privacy-compliant by afterthought. PETs are the technical foundation that makes that future possible. Start exploring them today — your future self (and your users) will thank you.